Platform release notes
These release notes describe recent changes to Harness Platform.
- Progressive deployment: Harness deploys changes to Harness SaaS clusters on a progressive basis. This means that the features described in these release notes may not be immediately available in your cluster. To identify the cluster that hosts your account, go to your Account Overview page in Harness. In the new UI, go to Account Settings, Account Details, General, Account Details, and then Platform Service Versions.
- Security advisories: Harness publishes security advisories for every release. Go to the Harness Trust Center to request access to the security advisories.
- More release notes: Go to Harness Release Notes to explore all Harness release notes, including module, delegate, Self-Managed Enterprise Edition, and FirstGen release notes.
Important feature change notice
This is a notification for a feature change aimed at enhancing your experience with Harness. Here's what you need to know:
-
Harness uses connectors to external secret managers (e.g. Google Secret Manager or Hashicorp Vault) to resolve/store secrets used by pipelines and elsewhere in the Harness platform. External secret manager connectors require configuration, including a means to authenticate to the external Secret Manager. On December 11, 2023, Harness added a restriction that users can only use Harness Built-in Secret Manager to store authentication credentials for access to the corresponding Secret Manager.
-
Continuity Assured: There is no impact on your existing pipelines. They remain compatible with the way secrets were referenced before this feature change. Note that this includes using an external secret manager other than the Harness Built-in Secret Manager to store the authentication secret.
Why did Harness make this change?
Our previous setup allowed configurations where credentials from one secret manager were stored within another, resulting in complexities that could be challenging to navigate. Moreover, these configurations might introduce vulnerabilities, posing potential security risks. For example, in a recent incident, our thread pool designated for secret manager resolution was exhausted.
Moving forward, we've implemented several validations, such as the disabling of self-references. Furthermore, with the introduction of the aforementioned restriction on secret managers, configurations is simpler to comprehend and maintain. This change aims to streamline the process, enhancing clarity and reducing potential security vulnerabilities.
Below is further explanation for each type of secret manager Harness currently supports and the changes associated with it.
-
Harness supports three authentication methods for AWS Key Management Service (KMS) and AWS Secrets Manager:
-
AWS Access Key: Access Key Id, Secrets Access Key, and AWS ARN need to be stored in Harness Built-in Secret Manager.
-
Assume IAM role on delegate: AWS ARN must be stored in Harness Built-in Secret Manager.
-
Assume Role using STS on delegate: AWS ARN must be stored in Harness Built-in Secret Manager.
-
-
Harness supports the following five authentication methods for Hashicorp Vault:
- AppRole secret IDs must be stored in the Harness Built-in Secret Manager.
- Token secret IDs must be stored in the Harness Built-in Secret Manager.
- AWS Auth secret IDs must be stored in the Harness Built-in Secret Manager.
- Vault Agent: Secret storage is not required in the Harness Built-in Secret Manager.
- Kubernetes Auth: Secret storage is not required in the Harness Built-in Secret Manager.
-
Harness supports two authentication methods for Azure Key Vault:
- With the credentials option, the Azure Authentication key must be stored in the Harness Built-in Secret Manager.
- With the credentials of a specific Harness Delegate option, secret storage is not required in Harness Built-in Secret Manager.
-
Harness supports only one authentication method for GCP Key Management Service, for which the GCP KMS Credentials file must be stored in the Harness Built-in Secret Manager.
-
Harness supports two authentication methods for GCP Secrets Manager:
- With the credentials option, the Google Secrets Manager Credentials File must be stored in the Harness Built-in Secret Manager.
- With the credentials of a specific Harness Delegate option, secret storage is not required in Harness Built-in Secret Manager.
-
For Custom Secrets Manager, if any secret is needed in the template as a variable, then it can only be stored in the Harness Built-in Secret Manager.
Deprecation notice
The following deprecated API endpoints are longer supported:
- [GET | PUT | POST | DELETE] api/resourcegroup/{identifier}
- POST api/resourcegroup/filter
- GET api/resourcegroup
December 2024
Version 1.69.x
Fixed issues
- Resolved an issue where the secrets created were not appearing in the “Referenced By” section of the connector. This was solved by updating the entity setup to support cross-scope references. With this fix, newly created secrets are now correctly displayed in the “Referenced By” section as expected. (PL-55818, ZD-67675)
New features and enhancements
- Successfully onboarded DB-DevOps (DBOPS) to Custom Dashboards. (PL-58911)
Version 1.68.x
Fixed issues
- Resolved an issue in the pipeline approval stage where Slack notifications were delayed by up to 10 minutes after the approval event. With this fix, Slack notifications are now sent instantly once the pipeline approval stage is issued. (PL-58801, ZD-72930)
New features and enhancements
- Introduced enhanced support for the variables in the resource group allowing restriction of access to
specific variableswithin the scope. Previously, users had access to either all variables or none. This update enables fine-grained access control, enabling users to select specific variables for controlled access across their organisation, account or project scope. (PL-58267)
Version 1.67.x
Fixed issues
-
Resolved an issue in the LDAP APIs to ensure proper handling of
Content-Type: application/json. This fix allows theTry Nowfunctionality in the API documentation to work correctly. (PL-58671, ZD-73126) -
Fixed an issue in MS Teams notifications where the
View Detailsbutton generated a malformed URL, causing a 404 error. (PL-58643, ZD-73591) -
Resolved an issue where certain failing connectors were throwing internal errors due to an edge case. (PL-58518)
-
Temporarily disabled the
Planspage in Account Settings behind a feature flag to address a CORS issue that was blocking access to subscription plans. (PL-58059, ZD-72115) -
Fixed an issue where users with appropriate permissions in parent scopes could not view YAML differences in the Audit Trail for accessible resources. (PL-58111, ZD-72001)
-
Enhanced access control for listing secrets across all scopes. Users will now only see secrets they have permission to access when performing an
ALL scopeslist operation, ensuring stricter RBAC compliance. This fix is currently behind the feature flagPL_ADD_RBAC_CHECK_SECRETS.. Contact Harness Support to enable it. (PL-57808, ZD-71673) -
Added support for runtime variables with default and allowed values in Custom Secret Manager connectors. (PL-58460, ZD-73094)
-
Resolved an issue where multiple accounts, including Wells Fargo and Verint, experienced delegates returning a
DEFAULT_ERROR_CODEwhen polling for tasks. This fix ensures delegates can execute tasks without errors. (PL-58573, ZD-73427)
New features and enhancements
-
Enhanced AWS Secrets Manager integration to support secret updates using the
secretsmanager:PutResourcePolicypermission. The appropriate request type (UpdateSecretorPutSecretValue) is now determined based on theusePutSecretflag in the connector configuration. This item requires Harness Delegate version 24.11.84500. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-58652) -
Optimized role assignment deletions by replacing the inefficient
findAllAndRemovemethod with remove. This improves database performance by avoiding unnecessary data fetching during deletions. (PL-56385) -
Upgraded the
io.netty:netty-commonlibrary to version4.1.115to address security vulnerabilities, includingCVE-2024-47535, ensuring enhanced application security and compliance. (PL-58550) -
Cross-module pipeline executions dashboards includes the ability to run ad-hoc queries for pipeline, stage, and step level views and allow cross module analysis. This includes one OOTB dashboard for pipeline executions, one for stage executions and another for step executions. (PL-50496)
November 2024
Version 1.65.x
Fixed issues
-
Enhanced delegate task logging by including the delegate's name along with the delegate ID. This improvement provides greater clarity and traceability, allowing for quicker issue identification and resolution. (PL-58095)
-
Resolved an issue in the List Users in User Group API where filtering by email returned incorrect results. The API now accurately lists only users who are part of the specified user group when using email filters. (PL-58049, ZD-72077)
-
Added support for OIDC authentication in the audit log streaming flow for AWS connectors (PL-57718)
New features and enhancements
-
Upgraded Spring Framework to version
6.1.x, along with updates to dependencies for improved compatibility and security. This item requires Harness Delegate version 24.11.84500. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-58254) -
Resolved a high-severity vulnerability (CVE-2024-7254) in the Delegate by upgrading
protobuf-javato version3.25.5. This item requires Harness Delegate version 24.11.84500. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-57351, ZD-70765) -
Increased the entity limits for Service Accounts, API Keys, and Tokens to 6000 per account. This update improves scalability and accommodates growing usage needs. For more details, please refer to the documentation. (PL-56430)
-
Upgraded the Java version to
17.0.11_9-jre-ubi9-minimalin the Delegate base image to address security vulnerabilities, includingCVE-2023-22041. This item requires Harness Delegate version 24.11.84500. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-55499) -
Upgraded
com.nimbusds_nimbus-jose-jwtto version9.37.2to addressCVE-2023-52428. This item requires Harness Delegate version 24.11.84500. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-51347)
Version 1.64.x
Fixed issues
-
The delegate name is now displayed in the UI whenever a connector test fails, provided the validation task was acquired by a delegate. This enhancement offers better visibility into which delegate handled the task during troubleshooting. This change requires Harness Delegate version 24.11.84304. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-56483, ZD-64425)
-
The
/.wellknown/jwksendpoint for OIDC now correctly exposes the "alg" value as "RS256" instead of "RSA256". This update ensures compatibility with standard OIDC configurations. (PL-58029) -
In the Resource Group Details page, when "All" is selected for resources, the options to specify environments by tag, type, or individually (+ Add button) are now hidden. This update prevents unintended configurations when managing resources in bulk. (PL-58108, ZD-72184)
-
Resolved an issue where the Event Summary link under Audit Logs would cause the page to break when a new, unhandled action was onboarded. The Event Summary now displays "N/A" in line with the Audit Logs page. (PL-57850)
New features and enhancements
-
GCP GCS Audit Streaming now supports Manual Credentials and IAM Delegate authentication, in addition to the existing OIDC-based authentication. This enhancement offers greater flexibility in authentication options. (PL-52059)
-
Added support for
Connection via Platformfor AWS Secrets Manager, AWS KMS and GCP KMS using theOIDC method, enabling users to connect directly through the Harness platform without requiring a delegate. (PL-52058) -
Added a new scope query parameter to the
listDelegatesendpoint. When set to true, this parameter enables listing delegates across hierarchical scopes (Account, Org, Project). By default, scope is set to false. This change requires Harness Delegate version 24.11.84304. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-57724) -
Upgraded the base image for
delegate,delegate-minimal,ci-addon, andlite-enginefromredhat/ubi8-minimal:8.8toredhat/ubi8-minimal:8.10. This update enhances security and compatibility with the latest UBI version. This change requires Harness Delegate version 24.11.84304. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-58062) -
Removed delegate and watcher JARs along with client tools from the delegate proxy in SMP. This update reduces the proxy footprint and optimizes performance. (PL-58052)
-
Updated the
delegate/ringsAPI to return the immutable delegate version instead of the legacy delegate version. Additionally, theconnected-ratio-with-primaryandconnected-delegate-ratioAPIs have been removed. This change requires Harness Delegate version 24.11.84304. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-57518)
October 2024
Version 1.62.x
Fixed issues
-
Resolved an issue where code base cloning steps failed due to class package changes, causing deserialization errors. Aliases have been added to ensure successful deserialization, improving build stability and preventing timeouts in clone code base steps. (PL-57778, ZD-70731, ZD-71581, ZD-71589, ZD-71593, ZD-71596, ZD-71597, ZD-71599, ZD-72110)
-
Removed the restriction on the Content-Type header for the Delegate metrics endpoint. The endpoint now accepts any Content-Type, enabling compatibility with tools like Dynatrace ActiveGate for metrics collection. (PL-57704, ZD-71319)
-
Enhanced query performance to prevent timeouts when filtering large numbers of user groups inherited in child scopes. Listing user groups now completes efficiently even with high volumes. (PL-57595, ZD-71170)
-
Removed restrictions on the Delegate metrics API endpoint, allowing requests with any Content-Type header. This update supports improved compatibility with monitoring tools like Dynatrace. This change requires Harness Delegate version 24.10.84200. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-57704, ZD-71319)
New features and enhancements
- Set limits on the number of delegates and delegate tokens allowed per account and per scope. The current limit is set to 10,000. This change requires Harness Delegate version 24.10.84200. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-56296)
Version 1.60.x
Fixed issues
-
Fixed an issue where delegate restarts during pipeline execution were incorrectly labeled as disconnections. The error message now correctly states delegate restarted while executing to help users identify the root cause related to their infrastructure. (PL-57421, ZD-70611)
-
Fixed an issue causing the Cloud Credits page to break in the QA environment. The issue was resolved by updating the path URLs with a
. +configuration change to ensure correct routing. (PL-57317) -
Made UI improvements to the Cloud Credits page, including enabling the TimeRangePicker for free subscriptions and increasing the page size to display all organizations and projects in dropdowns. (PL-56928)
Version 1.59.x
New features and enhancements
-
Updated the description and UI label for the
rotationTimeStampfield in the Rotate Token API. This update clarifies that the input is for setting the expiry time of the old token being rotated, ensuring clearer understanding during token rotation. (PL-56558, ZD-69048) -
Implemented a limit on the number of delegates and delegate tokens per account and per scope. The maximum number of delegate tokens is now set to 10,000 to ensure better management and scalability. This item requires Harness Delegate version 24.10.84104. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-56296)
-
Upgraded the
bitnami/minioimage to version2024.6.29-debian-12-r0to address multiple high and critical vulnerabilities, ensuring improved security and compliance. (PL-56127) -
Removed the outdated static HTML page (
https://app.harness.io/ng/static/versions.html) that displayed versions of various NG services. Customers are now advised to check deployed service versions from their Account Settings page in NGUI. (PL-52144) -
Upgraded the
com.nimbusds_nimbus-jose-jwtlibrary to version9.37.3to address high-severity vulnerabilities, including CVE-2023-52428, which could lead to denial of service through resource consumption. (PL-51347, ZD-70765) -
Enhanced Notification Support: Harness now seamlessly integrates with Microsoft Workflows to create and manage notifications, in addition to Microsoft Office 365 connectors. (PL-55565, ZD-66761, ZD-66985, ZD-67032, ZD-67378, ZD-68690)
Fixed issues
-
Fixed an issue causing the Cloud Credits page to break in the QA environment. The issue was resolved by updating the path URLs with a
. +configuration change to ensure correct routing. (PL-57317) -
Improved error messaging for pipeline execution failures when the delegate cannot reach the build pod. This enhancement helps users quickly identify connectivity issues between the delegate and build farm, improving troubleshooting and reducing impact on user experience. (PL-57241, ZD-68383, ZD-69998)
-
Fixed an issue with Cloud Credits reporting for the DataRobot account, where usage data was not displaying correctly. Updated the licenseUsageAPI logic to aggregate results by timestamp and CIOsType, and adjusted the license_Usage_Yearly table to account for leap years. (PL-57023)
-
Corrected the API documentation for the Audit Event API. The yamlDiffRecord field was incorrectly listed in the response and has been removed from the docs. Additionally, the missing auditYaml API endpoint has been added to the documentation for retrieving YAML differences. (PL-56934, ZD-69812)
-
Fixed several usability issues in the Roles Reusability feature, including auto-refetch failures in the Active User Lists view, non-functional Cancel buttons in the Assign Roles modal, and the unnecessary Back button in the Role Assignments modal. (PL-56146)
-
Implemented an RBAC check across all scopes when listing delegates and delegate tags. Users will now only see delegates they have access to in the current scope. This fix is currently behind the feature flag P
L_RBAC_CHECK_UP_THE_HIERARCHY_DELEGATE. Contact Harness Support to enable it. (PL-55748, ZD-67385) -
Improved error messaging for the
<+secrets.getValue(secretlocation)>expression to provide clearer feedback when a secret is not found. The updated message now states, "The secret has not been found," and includes the full computed path for better troubleshooting. This item requires Harness Delegate version 24.10.84104. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-51900, ZD-65130, ZD-69181)
September 2024
Version 1.57.x
New features and enhancements
- Upgraded
org.clojure:clojurefrom version 1.9.0 to 1.11.4 to address security vulnerabilities, including CVE-2024-22871, which could lead to a denial of service (DoS) attack. (PL-56307)
Fixed issues
-
Resolved an issue in FileStore where tag values were not displayed in the tag hover for files. The custom logic for rendering tags has been replaced with a standard Tags component, ensuring that both tag names and values are correctly shown. (PL-56940, ZD-69741)
-
Fixed an issue on the Freeze page where long names and identifiers caused text overlap in the UI. A maximum width has been set for the freeze name cell, with the full name and identifier now visible on hover. (PL-56843, ZD-69083)
Version 1.56.x
New features and enhancements
-
Improved error messaging for Custom Secrets Manager with Template to provide clear guidance when secrets are referenced from a lower scope. Users are now directed to the correct configuration using the provided documentation for prefixing secrets.
-
Added support for v1 APIs in template-service, ng-manager, platform-service, and pipeline-service for Istio version 1.19.0 and above. If you are running istio >= 1.19.0, add the following override in your
override.yamlfile to access V1 APIs. (PL-50528, ZD-65579)global:
istio:
enableRegexRoutes: true -
Fixed an issue where Slack could still be selected as a notification method at the project level, even after being disabled at the account level. Notification channel options are now controlled by Default Settings and must be enabled there to be available. (PL-48866, ZD-60861)
Fixed issues
-
Fixed an issue where users with the correct permissions were unable to delete resources in a Resource Group. (PL-56726, ZD-69369)
-
Fixed an issue where the AWS Secret Manager validation was failing due to regions being passed instead of full URLs, causing connectivity errors in delegate logs. The region is now correctly converted to a URL, preventing perpetual task failures. (PL-55740, ZD-67142, ZD-67150)
-
Enhanced webhook notification handling to support secrets in headers, enabling proper decryption of Authorization and other header values stored in the Harness Secret Manager. This ensures seamless webhook triggering without requiring hardcoded values. (PL-55319, ZD-65913)
Version 1.55.x
Fixed issues
-
Resolved consistent proxy authentication issues seen after delegate upgrade by removing unnecessary environment variable expansion and adding URL encoding for special characters. The
PROXY_PASSWORDenvironment variable is now handled correctly, ensuring proper authentication without requiring expansion. This item requires Harness Delegate version 24.08.83802. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-56623, ZD-68887) -
Fixed an issue preventing Canny login from the Harness UI for customers using vanity URLs. The Canny login flow now correctly redirects to sso.html, enabling seamless access across all environments, including global gateway clusters and vanity URLs. (PL-55679, ZD-66968, ZD-67907)
-
Fixed an issue where pipelines could get stuck in the running state due to delegate task handling. A new flow has been introduced to recompute eligible delegates after 3 rounds of broadcast, ensuring tasks are acquired even if delegates restart. This fix is controlled by the
RECOMPUTE_ELIGIBLE_DELEGATES_LISTfeature flag and requires Harness Delegate version 24.08.83802. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-55249, ZD-66247)
Version 1.54.x
New features and enhancements
-
Upgraded the
dnsjavalibrary to version3.6.0to address CVE-2024-25638, which involved potential security vulnerabilities in DNS query responses. This item requires Harness Delegate version 24.08.83800. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-55721, ZD-63383, ZD-68810) -
Upgraded the Spring Framework libraries to version
6.0.18to address multiple critical CVEs reported by Prismacloud. (PL-38815, ZD-42531, ZD-44910, ZD-46364, ZD-50403, ZD-52222, ZD-53107, ZD-53760, ZD-55114, ZD-60387, ZD-61129, ZD-62327, ZD-62502, ZD-62674, ZD-62690, ZD-63256, ZD-63383)
Fixed issues
-
Added an index for Audit Logs to improve query performance and reduce CPU usage (PL-55486)
-
Fixed an issue where users without account-level access could still use account-level delegates when creating connectors at the org or project level. The delegate listing now respects RBAC permissions at each scope, ensuring proper access control. This item requires Harness Delegate version 24.08.83800. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-55748, ZD-67385)
-
Fixed an issue where adding a new tag using the mouse click in the Tags input box on Default Settings Page wasn't working. Users can now create tags using both mouse clicks and the ENTER key. (PL-56098)
-
Updated the delegate expiration logic to align with the 6-month support and 2-month upgrade policy. This ensures that delegates maintain compatibility and support within the specified time frame. This item requires Harness Delegate version 24.08.83800. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-56193, ZD-68597, ZD-69188, ZD-69266)
-
Resolved an issue causing SCM binaries to not be found during delegate startup with versions
24.07.83605and24.07.83606. Updated the handling of default values for built-in Docker environment variables to prevent delegate initialization errors. This item requires Harness Delegate version 24.08.83800. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-56209, ZD-68661) -
Fixed an issue where restarting a delegate with an account-level token incorrectly moved the existing project-level delegate group to the account level. The query for locating the existing delegate group has been updated to ensure that it correctly handles cases where the owner field is null, preventing unintended group migrations. This item requires Harness Delegate version 24.08.83800. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-56377)
August 2024
Version 1.53.x
New features and enhancements
- Upgraded the org.apache.cxf:cxf-core library from version 3.5.8 to 3.5.9 to address a security vulnerability (CVE-2024-32007). This upgrade enhances the security and stability of the application. (PL-55722, ZD-63383)
Fixed issues
-
Resolved an issue where not all user groups were visible in search results when inherited groups exceeded 1000. The search now displays a higher number of inherited user groups, ensuring comprehensive visibility for all user groups across your organization. (PL-56021, ZD-68131)
-
Fixed an issue where installing or upgrading SMP to version 0.19.0 would fail when
harness-secretswas disabled. This issue was due to a version inconsistency in the common chart used by Helm, which has now been resolved by adjusting the chart hierarchy. (PL-56179)
Version 1.52.x
New features and enhancements
- The BouncyCastle library has been upgraded from version
1.76to1.78to address several medium-severity CVEs (CVE-2024-29857, CVE-2024-30171, CVE-2024-30172) and enhance overall system security. (PL-51346)
Fixed issues
-
The
displaynameattribute from SAML assertions is now honored for new JIT-provisioned users logging in via SAML. This ensures that usernames are correctly updated to reflect the displayname attribute, addressing inconsistencies in user names. (PL-55616) -
The delegate initialization process has been moved from a background thread to the start of application. This change addresses issues with health check failures during startup by ensuring that delegate registration, websocket establishment, and heartbeat scheduling are completed before health checks are performed. This item requires Harness Delegate version 24.08.83700. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-55905, ZD-67667)
Version 1.51.x
New features and enhancements
-
Improved delegate cache to reduce cache misses and optimize performance. This update ensures more reliable and efficient caching, addressing issues identified in recent incidents. (PL-55626)
-
Introduced a new feature in the Connector details Page that supports favorites. You can now mark connectors as
favorites, making it easier to filter and manage your preferred connectors for a more streamlined experience. (PL-55460) -
Enhanced AppRole token cache for HashiCorp Vault: Updated the cache key calculation to include secretId and approleId. This change fixes a problem where tokens were not being refreshed correctly. Now, the cache accurately reflects the latest credentials, ensuring secure and reliable token management. This item requires Harness Delegate version 24.07.83605. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-55567, ZD-65493)
-
Added proxy configuration support for external notification channels in SMP. To address issues faced by customers who operate in air-gapped environments, we've introduced proxy settings for the platform service. By updating the override file with proxy details, notifications via MS Teams and Slack will now function correctly even when behind a proxy. This feature is available in SMP version 0.19.0. This item requires Harness Delegate version 24.07.83605. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-48415, ZD-59707, ZD-62139)
Fixed issues
-
Enhanced validation on the User Group Form to provide accurate notifications when no users are selected or if only a search query is entered. This change improves user experience and form accuracy. (PL-55793)
-
Fixed issue with delegate creation scope where delegates were being created at the account level instead of the project level. The resolution ensures that delegates are correctly installed in the intended scope, particularly when creating new orgs or projects and installing Kubernetes delegates via YAML. (PL-55615)
-
Optimized query performance for
delegateConnectionResults. Added a new index based on delegateId and criteria to improve query efficiency and reduced CPU usage. Updated cache keys to include accountId for better indexing and cache utilization. This change addresses high query volume and CPU spikes previously observed. (PL-52071) -
Resolved issue with Rollout deployment logs where logs were not available or expandable. This problem, caused by a race condition between stream closure and log dispatching, has been fixed. Logs will now display correctly even under heavy load. This item requires Harness Delegate version 24.07.83605. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-55512, ZD-66330)
July 2024
Version 1.49.x
New features and enhancements
- We have added a security check to restrict SAML assertions to a single login. Any attempt to reuse a SAML assertion within its expiry period will now be rejected by Harness during login. Currently, this feature is behind the feature flag
PL_ENABLE_SAML_ASSERTION_CACHE. Contact Harness Support to enable the feature. (PL-55247, ZD-66114)
Fixed issues
-
SAML groups were not being picked up by Harness due to a regression introduced with recent changes in syncing users in SAML user groups. Identified and resolved the issue, ensuring that SAML groups are now correctly synced with Harness. (PL-55507, ZD-66567, ZD-66882)
-
SCIM sync issues were occurring due to incorrect handling of
orgIdentifierandprojectIdentifier. Updated the query to correctly handle cases whereorgIdentifierandprojectIdentifierare null. (PL-55444, ZD-66712) -
Users were able to see the enable/disable option for AIDA at the project level, even if AIDA was disabled at the account level. Implemented a change to display an error message when users attempt to enable AIDA at the project level if it is disabled at the account level. (PL-48296)
Version 1.48.11
New features and enhancements
-
Upgraded the
io.netty_netty-codec-httplibrary to address a medium-severity issue. The version has been updated from 4.1.101.Final to 4.1.108.Final. (PL-51350) -
Upgraded the
org.apache.cxf_cxf-corelibrary from version 3.5.5 to 3.5.8 to address a medium-severity issue CVE-2024-28752. (PL-51348, ZD-66657) -
Reduced delegate liveness probe failure time. Previously, delegates had a 15-minute window to send heartbeats before the liveness probe failed, leading to a delegate restart. This time has now been reduced to 5 minutes to ensure quicker detection and response to heartbeat failures. This item requires Harness Delegate version 24.07.83605. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-52037)
Fixed issues
-
Clicking a role after scrolling distorted the viewport. The issue with viewport distortion on the Roles page has been fixed. (PL-52063, ZD-65768)
-
Tokens could not be created via API from the API docs because the required fields were missing. Added the necessary required fields to the Create a Token page in the API docs, allowing tokens to be successfully created via the API. (PL-51974, ZD-65569)
-
The Cancel button was not working while creating a connector via YAML. Updated the behavior of the Connectors page YAML editor to match that of other pages. The Discard button on the YAML editor page now exits back to the previous page. (PL-42928)
-
Legacy delegates were unable to download the SCM binary. This issue has been resolved. (PL-55263, ZD-66357, ZD-66361)
-
Users were not being created in Harness FirstGen after being provisioned in NextGen. Updated the user provision field to ensure that users are properly created in Harness FirstGen after being provisioned in NextGen. (PL-52142, ZD-65604)
-
Users encountered a
Media not founderror when clicking the +Dashboard button and in the About the Dashboard dialog. Removed missing Dashboard tutorial videos, resolving theMedia not founderror. (PL-50890)
Version 1.45.5
New features and enhancements
-
The
terminationGracePeriodSecondsfor delegates has been increased from 10 minutes to one hour. This enhancement allows delegate pods to wait up to an hour before being forcibly terminated during regular scale-downs or upgrades, ensuring smoother transitions and minimizing potential disruptions. (PL-51534, ZD-63917) -
Added support for Harness Secret Manager decryption for notifications. Harness-managed secrets used in notifications are now decrypted using Harness Manager, enhancing security and functionality. (PL-41880)
-
Modified the unique index for delegate token names. The default token name in each scope will now be
default_tokeninstead ofdefault_token_org/project. This change applies only to new projects and organizations; existing projects and organizations will retain their current token names. This item requires Harness Delegate version 24.07.83404. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-51151)
Fixed issues
-
Connectors could be deleted even if they had existing secrets. This issue has been resolved, and now AWS Secret Manager Connectors cannot be deleted if they contain existing secrets. (PL-52067, ZD-65772)
-
Resource Scope was deleting projects. Searching for a project and then selecting it would remove all previously selected projects. Improved the project selection process in org scope Resource Groups to match the flow of project selection in account scope Resource Groups. This change resolves the issue and ensures previously selected projects remain intact when new ones are added. (PL-51988, ZD-65620)
-
Public access on resources was not functioning correctly when a project had multiple public resource types. Only the first resource type marked as public was registered internally in Access Control. This issue has been resolved. Now, public access is correctly registered for all resource types marked as public within a project, ensuring that every public resource type works as expected. (PL-51797)
-
SSH type deployment errors were not providing clear information, and delegate tasks continued beyond the maximum broadcast rounds. The issue has been resolved by failing the delegate task after the maximum broadcast rounds are completed. A correct error message will now be displayed to improve clarity. (PL-51241)
-
The Explore Plans button failed to redirect to the Plans page. Resolved the button routing issue to ensure the Explore Plans button now correctly redirects to the Plans page. (PL-49190, ZD-62009)
-
New users accepting an invitation and landing on the Get Started page encountered a 404 error. New users will now be redirected to the correct page upon accepting an invitation. (PL-51173)
June 2024
Version 1.43.5
New features and enhancements
- Harness has improved the sorting functionality for the User Group List API. Previously, sorting was based exclusively on the
lastModifiedAttimestamp, managed by Spring, with millisecond precision. This approach assumed that no two entities would share the samelastModifiedAttimestamp. Harness has introduced a secondary sort field to act as a tiebreaker. This adjustment ensures a consistent and reliable order across queries, improving the overall stability and accuracy of paginated results. (PL-48886, ZD-61135)
Fixed issues
- The CI module on the Subscriptions page didn't display the Available credits summary card and Credits breakdown table. You can now view the Available credits summary card and Credits breakdown table when
PL_ENABLE_LICENSE_USAGE_COMPUTEis disabled. When the flag is enabled, the summary card and table are moved to the Cloud Credits page instead of Subscriptions page. (PL-51838, ZD-65108)
Version 1.42.4
New features and enhancements
-
upgrader_enabledis now set totruein the Terraform delegate download section of the UI gen installation file to enable automatic upgrades. (PL-51681) -
Due to a bug, users could be added to SSO linked User Groups from the Harness UI, which should not be allowed. The addition of users to any SSO linked user groups from the Harness UI is now restricted. (PL-51431)
Fixed issues
-
Performing actions within embedded dashboards now refreshes the user's active session, preventing unexpected logouts. (PL-50534, ZD-62334)
-
Kubernetes services were created during the startup of the delegate, causing the IP pool to be exhausted for NAB. The delegate has been updated to prevent the creation of Kubernetes services upon startup, resolving the issue with IP pool exhaustion. This item requires Harness Delegate version 24.06.83304. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-51550)
-
Delegates were running out of memory due to frequent connectivity checks. Optimized the connectivity check process to reduce memory usage, preventing the delegate from running out of memory. This item requires Harness Delegate version 24.06.83304. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-51418, ZD-63705)
Version 1.41.6
New features and enhancements
-
Service Account name and email fields are now exposed in the Role Assignment filter API, enhancing visibility and management. For more information, go to List Role Assignments by scope filter. (PL-50613)
-
Harness added v1 API support for
template-service,ng-manager,platform-service, andpipeline-servicefor Istio >= 0.19.0 version. If you are running Istio >= 1.19.0, add the following override in youroverride.yamlfile to enable the support. (PL-50528, ZD-62230, ZD-62846)global:
istio:
enableRegexRoutes: true
Fixed issues
-
Harness recently made to allow hyphens in the secret identifier. However, the internal validation in the pipeline was not updated, which caused an error when the secret identifier was passed in the pipeline. This issue has been resolved to ensure the internal validation as well for secret identifiers containing a hyphen. (PL-51073)
-
Incorrect filters were displayed for the
includeScopesfield in Resource Groups in the Harness UI. While it was possible to add only project-level resources to a Resource Group via API, this option was not available through the UI. An Include Org-level resources option is now available in the UI. Users can now uncheck this option to include only project-level resources in a Resource Group, without including Org-level resources, addressing the previously unsupported use case. (PL-50969, ZD-62817) -
Delegate logs were displaying entire bearer tokens when using the IDP connector. Added log sanitization to delegate logs to mask commonly used secret patterns. These patterns can be extended per-use-case by adding them to the
/opt/harness-delegate/sanitize-patterns.txtfile inside the delegate. This item requires Harness Delegate version 24.06.83003. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-47914, PL-50889, ZD-64069)
May 2024
Version 1.39.4
Fixed issues
-
Keyboard navigation was not functioning for the Add Users list when adding a new member to a user group, and uncontrolled form submission occurred when pressing Enter. Updated the Add Users list to support keyboard navigation. Additionally, the form now properly handles uncontrolled submissions when the Enter key is pressed, allowing users to select items using the keyboard without unintended form submissions. (PL-51168, ZD-62169)
-
Due to a bug, users could be added to SCIM-provisioned/externally managed user groups from the Harness UI, even though membership edits for externally managed groups were not allowed. The issue has been fixed, and adding users to externally managed user groups via the Harness UI is no longer supported. (PL-50663)
Version 1.38.2
Fixed issues
-
Invalid user search results were returned when querying from page
2or higher. Harness updated the search functionality to reset thepageIndexto0after adding or updating a search query, ensuring accurate search results even when thepageIndexis2or higher. (PL-50907, ZD-62990) -
Delegate registration was not failing for inactive accounts. Harness added a check during delegate registration to verify account status. Delegates will now fail to register for accounts marked as
DELETEDorINACTIVE. This item requires Harness Delegate version 24.05.83001. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-48082)
Version 1.37.7
Fixed issues
-
An
UUID may not be emptyerror occurred when configuring LDAP settings. This was due to the LDAP identifier being sent as an empty string instead of null if it didn't already exist. The issue has been resolved, and the identifier is now correctly sent as null, preventing the error. (PL-50657) -
The
getUserGroupListAPI was returning inconsistent results, such as missing groups, due to issues with the sorting functionality based solely on thelastModifiedAttimestamp. We've enhanced the sorting mechanism in the User Group List API by introducing a secondary sort field to serve as a tiebreaker. This ensures consistent and reliable ordering across queries, significantly improving the stability and accuracy of paginated results. (PL-48886, ZD-61135) -
Login issues occurred in NextGen when FirstGen delegates were scaled down because the LDAP Authentication task was initially sent to FirstGen Delegates. If a FirstGen delegate wasn't available, the task would expire before being sent to a NextGen delegate. Compounding the issue, the timer at the Gateway was set to expire before the delegate task, leading to failed login attempts. We have implemented a solution that prioritizes sending the LDAP Authentication task to NextGen delegates first if the feature flag
PL_USE_NG_DELEGATE_LDAP_AUTHis enabled, thereby enhancing the reliability of login processes in NextGen environments. (PL-48541, ZD-60437) -
Pod Disruption Budgets (PDBs) in the Harness namespace caused issues during patching cycles due to incorrectly targeted rules. Harness updated PDB rules for the
cloud-info,anomaly-detection,gateway, andnext-gen-uiservices to select the correct pods, ensuring smooth operations during maintenance activities. (PL-49350, ZD-62353)
Version 1.36.5
Fixed issues
-
When adding users to a User Group, the search string persisted in the input field even after a user was selected. We have updated the User Group Form page to automatically clear the search query once a user is selected, enhancing usability. (PL-49256, ZD-62169)
-
Account admins, with permissions to assign roles, could assign any available role to any user, group, or service account, leading to concerns over control and governance. We have introduced a new feature flag,
PL_HIDE_ACCOUNT_LEVEL_MANAGED_ROLE, which, when enabled, restricts the visibility of account-level Harness-managed roles. This flag is disabled by default to maintain existing permissions structures across all accounts. (PL-43907) -
Delegates with mTLS enabled were able to send a heartbeat to Harness Manager despite being configured with a non-agent endpoint. Resolved this by ensuring the
isNgflag is correctly propagated when delegates send heartbeats to Harness Manager. This item requires Harness Delegate version 24.04.82901. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-48891, ZD-60974) -
Intermittent socket timeout exceptions occurred in running pipelines due to secret decryption failures, triggering unnecessary re-broadcasts on the delegate side. Resolved the issue of intermittent secret decryption failures within pipelines, ensuring stable and uninterrupted pipeline execution. This item requires Harness Delegate version 24.04.82901. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-47940, ZD-58006)
-
Local login was failing for users assigned admin permissions via a user group. The method to verify if a user is an account admin only considered direct user assignments and did not account for user group roles. Revised the validation process to include both user and user group assignments when checking for admin status. Now, to be recognized as an admin, users must have the specific role assignments outlined below; assigning the
_account_adminrole alone is no longer sufficient for admin rights.-
Role:
_account_admin. -
Resource-group:
_all_resources_including_child_scopes,_all_account_level_resources.
This item requires Harness Delegate version 24.04.82901. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes.
-
April 2024
Version 1.34.2
Fixed issues
-
The link to Slack on the UI Help section was not functioning. The community link has been updated to ensure it works correctly. (PL-48948, ZD-61203)
-
When a new pipeline for approval was created, but the approval email was not being sent, preventing testing of the link within the approval email. Resolved this issue that prevented notifications from being sent to multiple emails configured in a user group for email notifications. (PL-48854, ZD-60366, ZD-61333)
-
2FA reset emails failed to display the QR code properly due to the recent deprecation of Google APIs. The method for generating QR codes has been updated, resolving the issue and ensuring QR codes are now correctly included in 2FA reset emails. This item requires Harness Delegate version 24.04.82804. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes (PL-48980, ZD-61314, ZD-61420, ZD-61486)
Version 1.33.5
New features and enhancements
-
We've added an optional registry mirror configuration for delegate
upgrader. If you use Docker pull through registry cache (https://docs.docker.com/docker-hub/mirror/), you can configureupgraderto use an optional registry mirror for your delegate images. For more information, go to Configure an optional registry mirror for delegate images. This item requires Harness Delegate version 24.04.82707. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-47920, ZD-59005) -
AWS Secret Manager connectors now support both plain text and encrypted type Access Key Ids. (PL-48420)
-
Docker delegate images are no longer pushed to
app.harness.io/registry. To pull images, usegcr.io/gcr-prod/harness/delegate:<IMAGE_TAG>. This item requires Harness Delegate version 24.04.82707. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-46947)
Fixed issues
-
2FA reset emails failed to display the QR code properly due to the recent deprecation of Google APIs. The method for generating QR codes has been updated, resolving the issue and ensuring QR codes are now correctly included in 2FA reset emails. This item requires Harness Delegate version 24.04.82707. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-48980, ZD-61314, ZD-61420, ZD-61486)
-
Email steps were failing due to the system's inability to find users with emails containing uppercase letters, as Harness converts and stores all emails in lowercase. (PL-48532, ZD-60291)
-
Reset password emails were being sent from the FirstGen system for all accounts, causing issues for accounts that are exclusively NextGen. Now, if an account is identified as NextGen only, the reset password emails are dispatched from the NextGen system, rectifying the issue for NextGen only accounts. (PL-38735)
-
Slack channel notifications failed due to an error related to explicitly setting the "Host" header as "hooks.slack.com". We have removed the explicit "Host" header setting to support both Slack-specific webhook URLs and regular URLs, resolving the issue in this version. This item requires Harness Delegate version 24.04.82707. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-47914)
-
Delegate utilization metrics failed to decrease below a set threshold, even when rejecting all tasks. To solve this, memory-based threshold checks have been removed from the delegate due to functional discrepancies. This item requires Harness Delegate version 24.04.82707. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-48781, ZD-60713)
-
In SCIM, creating a new user with special characters in their name failed, preventing the user from being added to Harness and resulting in discrepancies in user group membership between the Identity Provider and Harness. This item requires Harness Delegate version 24.04.82707. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-47614)
-
The audit trail filter did not include an option for the Token resource type, hindering the ability to filter for API token updates. Added a Token filter option to the audit trail, enabling users to specifically filter for Token & API Key updates through a dropdown menu. (PL-48606)
-
Users experienced authentication issues when switching the OAuth type from SAML, leading to incorrect OAuth authentication status displays. Implemented changes to accurately reflect the status (enabled or disabled) of OAuth authentication for users. (PL-48788, ZD-60869)
-
The feature flag subscription indicated it was expired, and the license was not updating automatically. Users had to manually pay each invoice after the billing cycle was completed. Users can now view the correct billing due date on their subscription page. Additionally, the system has been updated to automatically charge the credit card on file when an invoice is generated. (PL-48671, ZD-57836)
-
The delegate task rejection metric was designed to reflect tasks rejected by a delegate due to system-related reasons (such as lack of resources or exceeding the limit of parallel tasks) but did not include specific details like task type or task ID. Enhanced the task rejection metrics by adding
taskTypeandtaskIdlabels. This item requires Harness Delegate version 24.04.82707. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-48488) -
Users were being logged out when testing a Git connector with invalid credentials due to the Git client's 401 response being propagated to the UI. Implemented error handling to convert a 401 response from the test connection step to a 400, while preserving the original error message, preventing unintended user logouts. This item requires Harness Delegate version 24.04.82707. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-47753, ZD-58629)
Version 1.31.4
Fixed issues
-
Fixed an issue where the Delegate Selector dropdown wasn't populating delegates when roles were configured with specific delegates instead of all. (PL-48292, ZD-59504)
-
Fixed an issue where the scope was derived from the open URL instead of the WinRM Secret's scope when editing WinRM secrets through a reference component, causing secret edits to fail. Scope details are now picked up from the WinRM secret being edited. (PL-48323)
March 2024
Version 1.30.7
New features and enhancements
-
harness-ingress-controllerarguments are now configurable through overrides. (PL-46366, ZD-55035)They can be controlled by the following YAML configuration.
nginx:
controller:
watchNamespace: ""
updateStatus: true
httpPort: 8080
httpsPort: 8443
watchIngressWithoutClass: true
defaultSSLCertificate: ""
configMap: ""
defaultBackendService: ""
publishService: ""
electionId: ""
controllerClass: ""-
You can provide any extra arguments like this:
nginx:
controller:
extraCommandArgs:
- --argument=example-argument -
Ingress controller can now be deployed with a
ClusterRole:nginx:
clusterRole:
create: true
-
-
In the recent update to
ng-managerversion 1.28.0, we have implemented enhancements to the validation mechanism for secret identifiers. We now provide more flexibility and precision in validating secret identifiers, particularly regarding hyphen usage. While previously disallowed, secret identifiers can now contain hyphens. However, there are specific rules governing their usage. Hyphens are now permitted anywhere in the secret identifier, including at the end of the string. The updated validation allows for multiple occurrences of hyphens within the secret identifier. Secret identifiers cannot start with a hyphen, following best practices. This item requires Harness Delegate version 24.03.82600. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-46959) -
'Secret Identifier' will now allow
-(hyphen) when provided as user input. For more information, go to Entity identifier reference (PL-48009)
Fixed issues
-
The delegate metrics endpoint
/api/metricshad its content type set asapplication/json, causing scraping issues with certain versions of Prometheus due to content type incompatibility. Attempts to switch to text/plain resulted in a 406 response code. We have revised the endpoint to deliver metrics inplainText. You can now specify the desired content formatplainTextorJSONby setting the "Accept" header in your request, ensuring broader compatibility with different Prometheus versions. This item requires Harness Delegate version 24.03.82600. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-46976, ZD-57489) -
Actions to create, edit, or delete Streaming Destinations were not being recorded in Audit Trails. This issue has been fixed, and these actions are now correctly captured in Audit Trails. (PL-47910)
Version 1.29.6
Fixed issues
-
Upgrade attempts from Harness Helm Chart 0.13.4 to 0.14.0 or 0.14.1 resulted in change-data-capture pod failures. We have resolved the initialization issue with the change-data-capture pod, which stemmed from the fileLogging parameters. (PL-47993)
-
In the old Git sync flow, the system failed to fetch connector details because the
branchandyamlGitRefattributes were not included in the query process after the method was changed to utilize scope uniqueId and identifier. We have updated the system to account for thebranchandyamlGitRefparameters, ensuring connector details now load correctly. (PL-47942, ZD-58953, ZD-59089) -
The user aggregate API did not support selected view permissions, leading to errors when a user was granted view permission for specific user groups due to the lack of permissions on the
USERGROUPresource as a whole. We have resolved this issue by allowing users to be granted view permissions for selected user groups. Now, only those user groups specified will be visible to the user. (PL-31279) -
For customers who need to bypass mutual TLS (mTLS) authentication for Current Generation (CG) delegates, even with strict mode enabled on the account, Harness has introduced the feature flag
PL_DISABLE_MTLS_CHECK_ON_CG_DELEGATES. This update allows specific disabling of mTLS checks for CG delegates, providing greater flexibility in security settings. (PL-47825, ZD-58762, ZD-60565)
Version 1.28.11
New features and enhancements
-
You can now add multiple emails to User Group notifications. This support allows you to include Harness Users or add emails separated by commas. (PL-46480)
-
The UI has been updated to include an HTTP Event Collector (HEC) Auth Token option in the Splunk Connector, allowing users to select HEC-type authentication. (PL-46977)
-
Upgraded
org.eclipse.jetty.*from v9.4.53.v20231009 to 9.4.54.v20240208. (PL-47854) -
The delegate list page now shows the latest delegate version beside the New Delegate button. This will help you compare your delegate version with the latest supported delegate version. This item is available with Harness Platform version 1.28.11 and does not require a new delegate version. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-47049)
-
OPA policy enforcement has been introduced to three new entities, namely Service Accounts, API Keys, and Tokens. For Service Accounts and API Keys, naming convention policies are enforced, while for Tokens, Time-To-Live (TTL) policies are enforced. These enforcement mechanisms are seamlessly integrated into both create and update operations, ensuring adherence to predefined standards during the onSave action. (PL-41877)
-
Introduced separate environment variables to manage delegate resource thresholds for CPU and Memory when dynamic handling is enabled. Use
CPU_USAGE_THRESHOLDfor CPU control (default: no limit). UseMEMORY_USAGE_THRESHOLDfor memory control (default: 80%). If you are usingRESOURCE_USAGE_THRESHOLD(deprecated), it exclusively controls the memory threshold. This item requires Harness Delegate version 24.03.82502. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-47746) -
OPA policy enforcement has been introduced to three new entities: Service Accounts, API Keys, and Tokens. For Service Accounts and API Keys, naming convention policies are enforced, while for Tokens, Time-To-Live (TTL) policies are enforced. These enforcement mechanisms are seamlessly integrated into both create and update operations, ensuring adherence to predefined standards during the
onSaveaction. This item requires Harness Delegate version 24.03.82502. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-46778) -
Support added to enable OPA policy for naming convention enforcement while creating or updating a service account. This item requires Harness Delegate version 24.03.82502. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-46777)
Fixed issues
-
Delegate logs were unavailable due to the system not automatically switching to app.harness.io as the remote logging service when GCP was blocked by a firewall. The auto-switching mechanism for the remote logging destination is fixed, ensuring accessibility to delegate logs when GCP is blocked by a firewall. This item is available with Harness Platform version 1.28.11 and does not require a new delegate version. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-46958, ZD-57844)
-
Perpetual tasks experienced significant delays in reassignment after the current delegate was shut down. We have addressed the issue of prolonged delays in perpetual task reassignment following delegate shutdowns by increasing the frequency of cron jobs that reset the perpetual task state for reassignment. This item is available with Harness Platform version 1.28.11 and does not require a new delegate version. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-47781, ZD-58497, ZD-58522, ZD-58650)
-
Fixed the issue that allowed the creation of user Personal Access Tokens (PATs) at the organization and project scope via API, ensuring consistent listing and management in the UI. PATs can only be created at the account scope. (PL-47558)
-
Attempts to use the
harness_platform_userresource to create or delete users resulted in an error. The message "Request failed as you have an older version of an entity, please reload the page and try again" was displayed and the Terraform state went out of sync with Harness. This issue has been fixed. This item requires Harness Delegate version 24.03.82502. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes. (PL-39870, ZD-47107)
Version 1.27.10
New features and enhancements
-
Support added to enable OPA policy for TTL enforcement while creating or updating an API Key Token. (PL-46779)
-
Invitation emails now include the inviter's username and email address, enhancing clarity for recipients. (PL-47694)
Additionally, the name of the account to which the user is being added is now specified in the invite, providing better context for the invitation.
Fixed issues
-
After adding users to an Azure AD group, which then propagated to Harness, not all users were reflected in the "All Account Users" and "Harness Prod Users" user groups. The "Harness Prod Users" group, tied to SCIM, did not automatically include all newly created users in Harness, affecting the Harness STO module go-live. (PL-47669, ZD-55559, ZD-57091, ZD-58412, ZD-58486)
We have fixed this issue with concurrent updates to user groups during user synchronization through SCIM, ensuring complete sync of all users in user groups from Azure AD to Harness.
February 2024
Version 1.26.14
Fixed issues
-
Creating or updating a project with an org identifier absent in the account used to throw error code: 500. (PL-47059, ZD-58093)
Now, the UI displays the following improved error message if the provided org identifier is absent:
Organisation with identifier "OrgId" does not exist in accountIdentifier: "accountId". -
The retry interval for attempting to create or read secrets from HashiCorp Vault was fixed at 1 second after each failure. (PL-46595, ZD-57053)
The retry interval has now been modified to increase by a factor of 2 times the number of failures. Consequently, after the first failure, the second attempt will occur after a 2-second delay, and the third attempt will be made after a 4-second delay, enhancing the robustness of secret management operations.
This item requires Harness Delegate version 24.02.82402. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes.
-
When linking an SSO group with over 1,000 users, only 1,000 users were syncing in Harness due to a limitation with LDAP groups syncing. (PL-46492, ZD-56741)
Implemented LDAP to perform paginated queries by default for large groups, with a fallback to non-paginated calls, ensuring complete user synchronisation.
This item requires Harness Delegate version 24.02.82402. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes.
-
Pipelines were failing due to errors related to the inability to acquire delegate tasks. (PL-42600, ZD-54025, ZD-54324)
The logic for calculating CPU and Memory usage has been improved, specifically for scenarios utilizing the dynamic task request handling feature in delegates, enhancing the reliability of task allocation and pipeline execution.
This item requires Harness Delegate version 24.02.82402. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes.
Version 1.25.5
New features and enhancements
-
Harness has updated the default HPA in the Harness Delegate YAML to use
autoscaling/v2instead ofautoscaling/v1which was used in earlier delegate versions. (PL-43686)With this update, the delegate default scaling metrics are now 70% of CPU and 70% of memory utilization.
---
apiVersion: autoscaling/v2
kind: HorizontalPodAutoscaler
metadata:
name: kubernetes-delegate-hpa
namespace: harness-delegate-ng
labels:
harness.io/name: kubernetes-delegate
spec:
scaleTargetRef:
apiVersion: apps/v1
kind: Deployment
name: kubernetes-delegate
minReplicas: 1
maxReplicas: 1
metrics:
- type: Resource
resource:
name: cpu
target:
type: Utilization
averageUtilization: 70
- type: Resource
resource:
name: memory
target:
type: Utilization
averageUtilization: 70
---Since
autoscaling/v2has been GA with Kubernetes 1.23 and higher, if you have a Kubernetes version lower than 1.23, you must manually change theapiVersionin theHorizontalPodAutoscalerof your delegate YAML toautoscaling/v1.For more information, go to Configure Harness Delegate autoscaling using replicas for Kubernetes.
This update only affects new delegate installations. Your existing, running delegates are not affected.
-
Added ability to write delegate logs in JSON format using logstash-logback-encoder library. This can be useful if logs are injected into third party services like DataDog which works better with JSON format. (PL-43525)
This item is available with Harness Platform version 1.25.5 and does not require a new delegate version. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes.
-
Enhanced the
override-delegate-tagAPI documentation to include details onvalidForDaysandvalidTillNextReleaseparameters. Additionally, the default value forvalidForDayshas been updated to 180 days, extending from the previous 30 days. For more information, go to Override delegate image tag in the API documentation. (PL-46879)This item is available with Harness Platform version 1.25.5 and does not require a new delegate version. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes.
Fixed issues
-
Errors occurred when creating a connector with an identifier (Account, Organization, or Project Identifier) that did not exist, displaying a generic "something went wrong, please contact Harness Support" message. (PL-46909, ZD-57678)
The code has been updated to provide accurate error messages and the current status code when the provided identifiers are incorrect or absent, enhancing clarity and user guidance.
-
Delegates were restarting in the middle of execution, disrupting ongoing tasks. (PL-46793)
Implemented a fix to wait for the task response to complete before marking it as expired or failed during the delegate's unregistering process, preventing premature restarts.
This item is available with Harness Platform version 1.25.5 and does not require a new delegate version. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes.
-
API keys created using the harness_platform_apikey Terraform provider were expiring even when no expiration date was set. (PL-43308)
You can now view the API key expiration date at the top of the API Key table on the user profile page. Additionally, for API key’s tokens where the expiration was intended to be set as No Expiration, you can see the default expiration date, clarifying the token's validity period.
Version 1.24.7
New features and enhancements
-
You can now enable file logging for supported services through override in Harness Self-Managed Enterprise Edition (On-prem) installations. (PL-44211)
To enable file logging, add the following to your
override.yamlfile in theglobalsection:global:
fileLogging:
enabled: true
logFilename: /opt/harness/logs/pod.log #provide log filename
maxFileSize: 50MB #max single file size, for log archiving
maxBackupFileCount: 10 #max count of files
totalFileSizeCap: 1GB -
Added support for encrypted assertions in the SAML response. (PL-43353)
-
Added support for selecting the environment in the manual credentials option while creating an Azure key vault connector. (PL-46485)
Fixed issues
-
The authentication mechanism of a secret manager couldn't be changed from a non-password-based to a password-based mechanism due to a bug in the secret manager update API. (PL-46657)
This issue has been fixed, enabling the modification of the authentication mechanism for secret managers to a password-based mechanism.
-
Git connectors worked intermittently and failed with a
Please provide valid git repository url Provided repo url is invalid. Invalid request: Couldn't connect to given repoerror message. (PL-43598, ZD-55236)This issue has been resolved. Now, if there are multiple connectors whose secrets are stored in a secret manager connector, when you update the connector's secret, Harness updates the PPTs of all the linked connectors, along with the secret manager connector.
This item is available with Harness Platform version 1.24.7 and does not require a new delegate version. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes.
-
When linking an SSO group with over 1,000 users, only 1,000 users were syncing in Harness due to a limitation with LDAP groups syncing. (PL-46492, ZD-56741)
Implemented LDAP to perform paginated queries by default for large groups, with a fallback to non-paginated calls, ensuring complete user synchronization.
Version 1.23.5
New features and enhancements
-
You can now hide sensitive log information in the Harness UI based on regular expression patterns. (PL-46531, ZD-56849)
For more information, go to hide log information using regex patterns.
This item requires Harness Delegate version 24.01.82110 or later. For information about features that require a specific delegate version, go to the Delegate release notes.
Fixed issues
-
The
helm-init-containerimages lacked a versioned tag and the pull policy forwaitForInitContainerswas not configurable. This led to the usage of unstable images in some places, which were not updated to the stable image because of the cached image with the same tag and image digest. (PL-46444)This has been resolved by adding configuration options for image, resources, and security, which can be controlled at global and service levels in the overrides and the versioned image of
helm-init-containeris now being used. The image pull policy is also set toAlwaysas the default.
January 2024
Version 1.22.3
New features and enhancements
-
Removed the unused
org.redisson:redissonlibrary dependency from the delegate. (PL-42485, ZD-53588, ZD-53760) -
Deletion of SCIM-managed user groups was not allowed. (PL-39439, ZD-53340)
You can now delete SCIM-managed user groups via the delete API for user groups.
infoHarness does not currently support the ability to delete SCIM-managed user groups in the UI.
Fixed issues
-
K8S_WATCHperpetual tasks remainedTASK_ASSIGNEDdespite being assigned to non-existent delegates. (PL-43973)This issue was fixed by implementing a CronJob to reset perpetual tasks associated with invalid delegates, ensuring proper handling of Kubernetes events.
This item is available with Harness Platform version 1.22.3 and does not require a new delegate version. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes.
-
Running
terraform applyfor an existing SSO-linked user group resulted in an empty user list. (PL-43763, ZD-55505)This issue has been resolved. Now, when the user group payload is SSO-linked, the existing users are maintained as is, and the users list in the payload is ignored.
- In cases where the existing user group is SSO-linked and needs to be overridden and delinked in the update payload, the existing users will be replaced with the users list provided in the payload.
-
The
platform-servicewas not publishing the response count metric. (PL-43123)This has been resolved, and the
platform-servicewill now consistently publish the response count metrics.
Version 1.21.5
Fixed issues
- Tooltips in the left navigation were incorrectly displayed behind the stage execution details panel. Now, tooltips are visible on the Execution page. (PL-43993)
- Fixed the ACL list roles API to correctly display
HarnessManaged,CreatedAt, andLastModifiedAtdate fields, ensuring accurate role management data in responses. (PL-43952) - Multi-select dropdowns would reset to the top after each selection. This issue is fixed for all multi-select dropdowns unless explicitly specified by the user. (PL-43925)
- When editing user group data, member data was not added as expected. Now, the user group data related to the user group members is not lost when the user group is updated. (PL-43855, ZD-55944)
- Fixed an issue where searching for user groups containing special characters resulted in a 500 error due to invalid regex patterns in the search term. Now, the
usergrouplist API validates regex patterns and provides a clear error message for invalid search terms. (PL-43761) - The Azure endpoints were not being set based on the Azure environment selected. This led to Azure connectors working correctly only for Azure public cloud and not for other variants of Azure cloud (like Azure Gov, Azure China, and so on). Now, the correct Azure resource manager endpoint will be chosen based on the environment selected in the connector. (PL-43333, ZD-54717)
Version 1.20.9
New features and enhancements
-
Configure an absolute session timeout for your account (PL-43587)
A new Absolute Session Timeout (in minutes) setting is available on the Authentication page. When the Absolute Session Timeout (in minutes) is set, users will be logged out of their account after the configured timeout, regardless of any activity.
The default absolute session timeout is 0, which means that it is not set. You can set this to a maximum of 4320 minutes (3 days). The field automatically converts the minutes you enter to higher units of time, and displays the result under the field. For example, if you enter 1440, the UI shows 1 day below the field.
noteWhen both the session inactivity timeout and the absolute session timeout are set, the condition that is met first will be honored.
-
You can now toggle between the legacy UI navigation and the new navigation by enabling the feature flag
CDS_NAV_PREFSfor your account. (PL-43772)
Early access features
-
Grant public access to Harness pipelines (PL-43499)
You can now grant public access to Harness pipelines. New settings on the Authentication page and in pipeline Advanced Options allow you to grant public access to pipeline executions.
When you activate the Allow public resources authentication setting, you can then enable public view for your pipelines by setting the Mark this pipeline for public view option in the pipeline's Advanced Options.
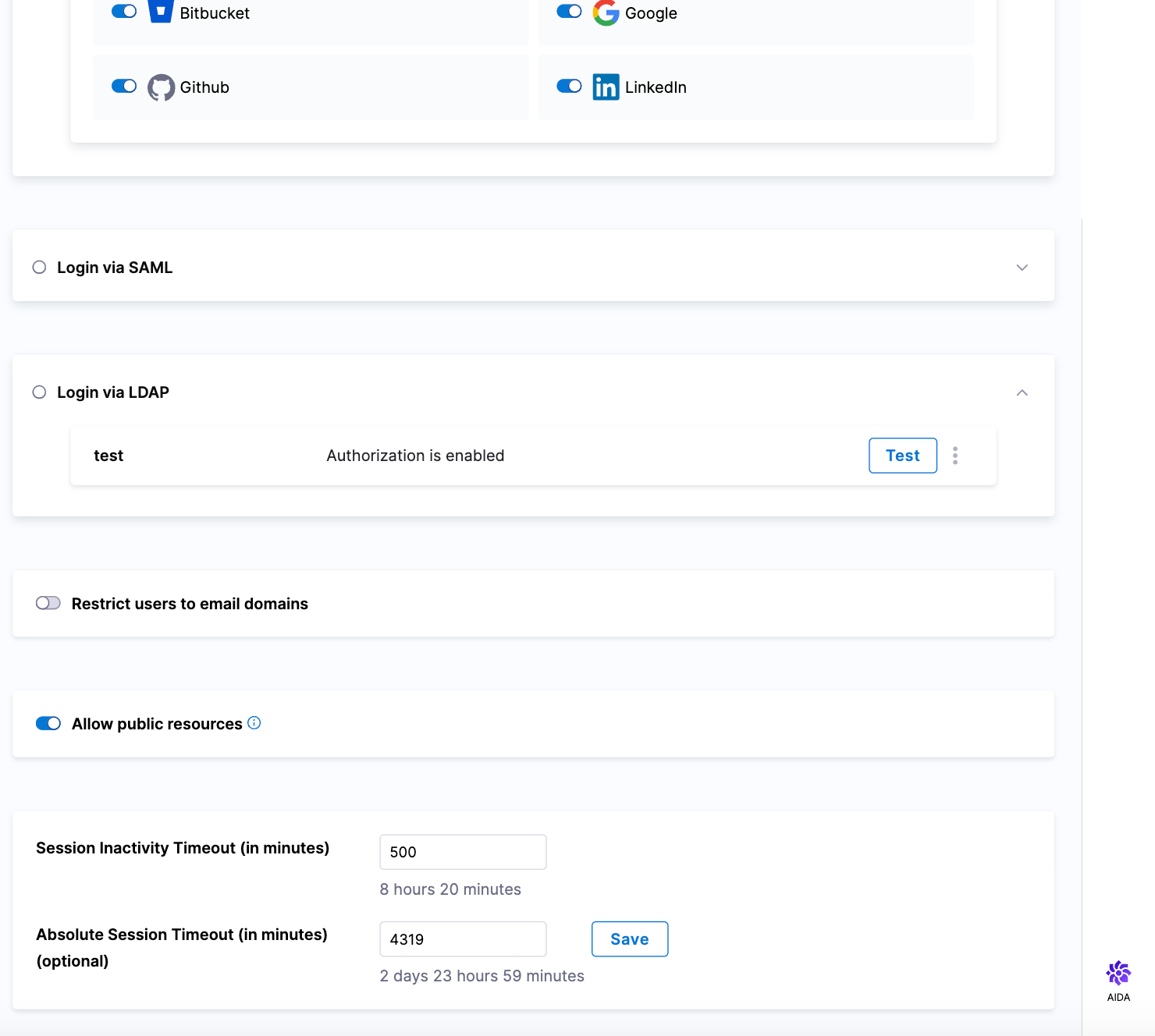
Pipeline executions for pipelines marked for public view will be accessible without the need to authenticate in Harness. You can share pipeline execution URLs, which include console logs for the pipeline steps.
For more information, go to Allow public access to pipeline executions.
This is behind the feature flag
PL_ALLOW_TO_SET_PUBLIC_ACCESS. -
Allowlist verification for delegate registration (PL-42471)
noteCurrently, allowlist verification for delegate registration is behind the feature flag
PL_ENFORCE_DELEGATE_REGISTRATION_ALLOWLIST. Contact Harness Support to enable the feature.Without this feature flag enabled, delegates with an immutable image type can register without allowlist verification. With this feature flag enabled, delegates with an immutable image type can register if their IP/CIDR address is included in the allowed list received by Harness Manager. The IP address/CIDR should be that of the delegate or the last proxy between the delegate and Harness Manager in the case of a proxy.
Harness Manager verifies registration requests by matching the IP address against an approved list and allows or denies registration accordingly. For more information, go to Add and manage IP allowlists.
This item requires Harness Delegate version 24.01.82108. For information about features that require a specific delegate version, go to the Delegate release notes.
Fixed issues
-
Intermittent errors occurred when pulling secrets from a Custom Secret Manager. (PL-43193, ZD-54236, ZD-54555, ZD-55919)
This issue has been resolved by adding a timeout (in seconds) to fetch secrets from a custom provider in the Custom Secret Manager settings. The process interrupts and fails when it takes longer than the configured timeout to fetch the secret. The default value is 20 seconds.
This item requires Harness Delegate version 24.01.82108. For information about features that require a specific delegate version, go to the Delegate release notes.
Version 1.19.6
New features and enhancements
- Upgraded MinIO to
bitnami/minio:2023.10.7-debian-11-r2. (PL-42019)
Early access
Allowlist verification for delegate registration (PL-42471)
Currently, allowlist verification for delegate registration is behind the feature flag PL_ENFORCE_DELEGATE_REGISTRATION_ALLOWLIST. Contact Harness Support to enable the feature.
Without this feature flag enabled, delegates with an immutable image type can register without allowlist verification.
With this feature flag enabled, delegates with an immutable image type can register if their IP/CIDR address is included in the allowed list received by Harness Manager.
The IP address/CIDR should be that of the delegate or the last proxy between the delegate and Harness Manager in the case of a proxy.
Harness Manager verifies registration requests by matching the IP address against an approved list and allows or denies registration accordingly. For more information, go to Add and manage IP allowlists.
Fixed issues
-
The delegate was rejecting tasks due to an issue where the CPU and memory calculation wasn't showing the latest usage value. This was caused by the dynamic request handling feature that rejects tasks if the CPU and memory usage exceeds a certain threshold. The pods weren't scaled by HPA because the CPU and memory usage within the pods was within the limit. (PL-42600, ZD-54025, ZD-54324)
Harness improved the CPU/Memory calculation algorithm, resolving the issue.
This item is available with Harness Platform version 1.19.6 and does not require a new delegate version. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes.
-
In the Add new Encrypted Text dialog, the Regions list for Google Secrets Manager integration included unsupported values.(PL-43575, ZD-55268)
This issue has been resolved and the Regions list has been updated with the correct GCP regions.
-
When Harness user groups were created during SCIM sync, dots were not converted to underscores in Harness for user group IDs. (PL-43576, ZD-55266)
This issue has been resolved. Now, SCIM group names that contain dots are converted to underscores in Harness for group identifiers. For example, a SCIM group named "abc.xyz" is created as follows:
UserGroupIdentifier: "abc_xyz"UserGroupName: "abc.xyz" -
Perpetual tasks weren't assigned after a delegate restart. (PL-43646, ZD-55426, ZD-55572)
Fixed race condition where a perpetual task was assigned at the same time as the delegate abruptly shutting down due to a pod restart.
This item is available with Harness Platform version 1.19.6 and does not require a new delegate version. For information about Harness Delegate features that require a specific delegate version, go to the Delegate release notes.
Version 1.17.8
New features and enhancements
- Upgraded the
yqlibrary from version 4.35.2 to 4.40.5. (PL-42548)
Fixed issues
-
For user groups provisioned from SCIM to Harness, for the corresponding user groups created in Harness, the user group
identifieris derived from the display name of the user group in the SCIM provider. Harness replaces.(dots) and-(dashes) with an_(underscore). All other special characters (#,?,%, and so on) and spaces are removed. Leading digits0through9and$are also removed. (PL-42535, ZD-53830, ZD-55294)All special characters except
.,-, and non-leading$and digits0through9are removed.Example 1: For a user group in SCIM with the name
Harness.Group?Next#Gen-First, the user group created in Harness will have theidentifier:Harness_GroupNextGen_First.Example 2: For a user group in SCIM with the name
123#One.$Two.$Three.123, the user group created in Harness will have theidentifier:One_$Two_$Three_123.The existing behavior of
.and-changed to_has been retained.The name of the corresponding user group created in Harness will retain the special symbols as present in the user group of the SCIM provider. Example: For a user group in SCIM with the name
Harness.Group?Next#Gen-First, the user group created in Harness will have the samename:Harness.Group?Next#Gen-First.This item requires Harness Delegate version 23.12.82000. For information about features that require a specific delegate version, go to the Delegate release notes.